Information Security
Saturday, March 2, 2019
Monday, February 5, 2018
How to DoS 29% of the World Wide Websites - CVE-2018-6389
According to wordpress.com, the WordPress platform powers 29% of the worldwide internet websites.
In this article I am going to explain how Denial of Service can easily be caused to almost any WordPress website online, and how you can patch your WordPress website in order to avoid this vulnerability being exploited.
It is important to note that exploiting this vulnerability is illegal, unless you have permission from the website owner.
While browsing a WordPress website, my attention was drawn to the following URL:
The load-scripts.php file receives a parameter called load[], the parameter value is 'jquery-ui-core'. In the response, I received the JS module 'jQuery UI Core' that was requested, as demonstrated in the following image:
Thursday, February 1, 2018
Gem in a box CSRF file upload - CVE-2017-14506
In this blog post I will give a short example of exploiting CSRF vulnerability on Geminabox.
So Geminabox is an application allows you manage your internal gems was vulnerable to CSRF on upload file.
In order to exploit the CSRF vulnerability I wrote really small tool called csrFile, which allows you to generate HTML that uploads any type of file to the supplied endpoint, you can check it out in the following link:
https://github.com/Quitten/csrFile
Usage: python csrFile.py <url> <filePath>
So using the following command, you can easily create an HTML document that exploits the CSRF attack and uploads malicious gem file to the targeted server:
python csrFile.py https://geminaboxserve/upload xss.gem
Then in case the victim will browse to the attacker's link that contains the HTML generated from csrFile, his browser will automatically will upload the attacker's malicious gem to geminabox system.
Note: it is possible to exploit persistent XSS attack (CVE-2017-14506) in that way as well.
So Geminabox is an application allows you manage your internal gems was vulnerable to CSRF on upload file.
In order to exploit the CSRF vulnerability I wrote really small tool called csrFile, which allows you to generate HTML that uploads any type of file to the supplied endpoint, you can check it out in the following link:
https://github.com/Quitten/csrFile
Usage: python csrFile.py <url> <filePath>
So using the following command, you can easily create an HTML document that exploits the CSRF attack and uploads malicious gem file to the targeted server:
python csrFile.py https://geminaboxserve/upload xss.gem
Then in case the victim will browse to the attacker's link that contains the HTML generated from csrFile, his browser will automatically will upload the attacker's malicious gem to geminabox system.
Note: it is possible to exploit persistent XSS attack (CVE-2017-14506) in that way as well.
Monday, October 30, 2017
Can you trust Facebook links?
While we are on Facebook, we are often share links to external sources, like Youtube, Google Drive, Instagram, or any other websites.
Many people think that Facebook links are quite reliable, but are they?
Facebook users can send those links via post or privately over Messenger, as you can see on the following images:
So how exactly preview link feature works?
Monday, September 18, 2017
Gem in a box XSS vulnerability - CVE-2017-14506
In this short blogpost I will give a short explain of XSS vulnerability i found on geminabox v0.13.5. which is a gems manager like rubygems.org so you can upload and download gems
Tuesday, August 18, 2015
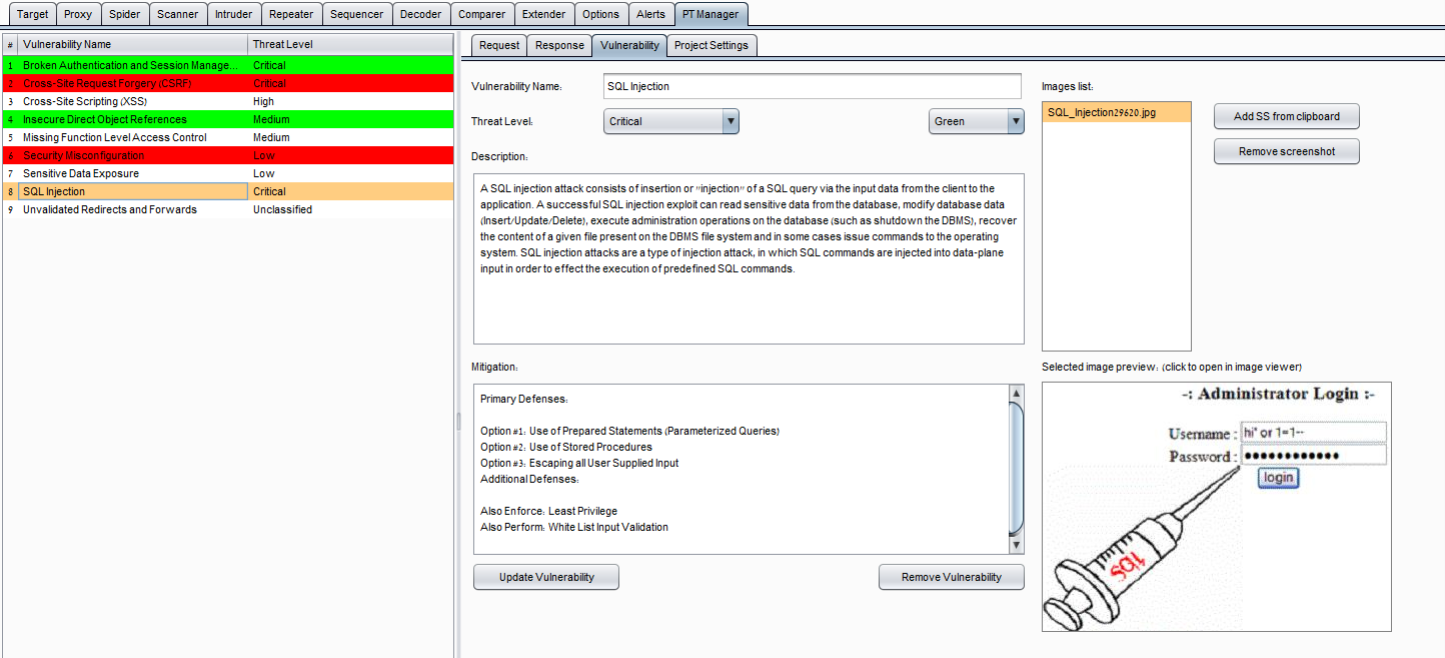
PT Vulnerabilities Manager - burp extension
Penetration test vulnerabilities manager extension for Burp Suite written in Jython developed by Barak Tawily in order to ease application security people manage vulnerabilities
Friday, February 20, 2015
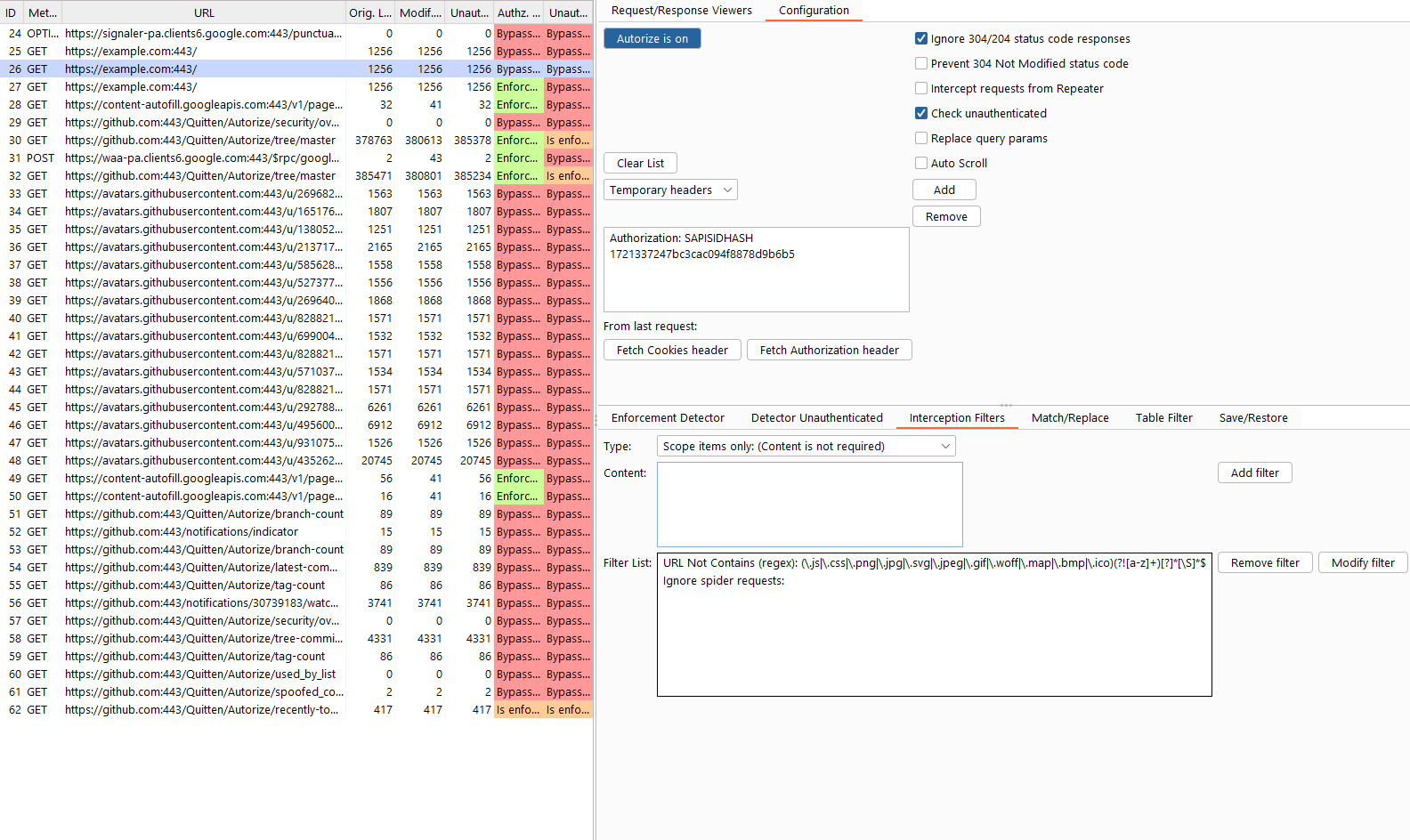
Autorize - automatic authorization enforcement detection extension for Burp Suite
Autorize
Github - https://github.com/Quitten/Autorize
Autorize is an automatic authorization enforcement detection extension for Burp Suite. It was written in Python by Barak Tawily, an application security expert at AppSec Labs. Autorize was designed to help security testers by performing automatic authorization tests.
Subscribe to:
Posts (Atom)